Largest darknet marketplace shut down by US, German law enforcement
Nano /etc/nginx/sites available/hideme. Tor hidden services allow various types of services web server, telnet server, chat server, etc to be operated within the Tor network. Please explain why or why not. For example, while venues can’t know exactly what proportion of their allowed max response time an LP is using to apply additional hold times, they could shorten that time as a way to at least reduce the possible length of hold times being applied – levelling the playing field. Here’s how to use a VPN to access the dark web. While dark web monitoring is a broad term that covers different services at different companies, it can generally be defined as a service that monitors the dark web for signs of stolen data, whether it’s stolen personal information for identity theft or administrator credentials for corporate networks. Table 1: 3 year GDS trend data for darknet drug market involvement across Europe. By default, in the latest version of Tor, you will get a v3 onion address that is 56 characters long. Due to the lack of reputation options on these vendor shops, it is hardly to check the authenticity of these shops for users. Want a Website Like This. The dark web and deep web are not the same — all sites on the dark web are technically part of the deep web, but much of the deep web is not part of the dark web. Discover our full product range now – from energy trading and reserve power, over spot market access and BRP services, to VPP as a Service. This case was brought in conjunction with the Joint Criminal Opioid and Darknet Enforcement J CODE Team. View or Download as a PDF file. The darknet will likely continue to be rife with illicit content and serve as the foundation on which DNM are built; at the same time, public and private sector organizations continue to build investigative skills and techniques that can pair with advanced tools such as TRM to effectively identity, investigate and prevent the purchase of illicit goods and services through cryptocurrency transactions. A lot of these criminal communities, especially trading in personal data and fraud materials, are perfectly happy to operate in plain sight. “Underground websites such as Silk Road and Silk Road 2 are like the Wild West of the Internet, where criminals can anonymously buy and sell all things illegal,” said HSI Associate Director Edge. This type of market has become increasingly popular due to its privacy features, making it an attractive option for those seeking to buy or sell items without leaving a digital footprint. Have you faced hardships while creating a dark web market or getting the most promising logo. We will update with new links as needed. It doesn’t need too much human intervention. Many onion services offered no or insufficient website content to categorize. Install Avast SecureLine VPN today to browse safely and securely, wherever your online travels take you. On the dark web, anything goes, whether it be illegal drug sales, hacker forums, or things much, much darker. 608921+00:00 running 252de61 country code: EE. The price of DeepOnion ONION is calculated in real time by aggregating the latest data across 2 exchanges and 2 markets, using a global volume weighted average formula. Group ties, however, allow perfect matching abroad to a minority of individuals who have access to them and can decide whether or not to exploit them. Then, it sequentially sends your request through three random relay servers. Loopholes exist, and if your government is motivated enough to track what you’re doing, they can.
Tor Hidden Services
Blacksprut, and Mega to fill the gap left by Hydra’s demise. He is the author of Linux Hardening in Hostile Networks, DevOps Troubleshooting, The Official Ubuntu Server Book, Knoppix Hacks, Knoppix Pocket Reference, Linux MultimediaHacks and Ubuntu Hacks, and also a contributor to a number of other O’Reilly books. Deep Web Radio is the dark web’s 24/7 onion radio link. Crypto may also be more susceptible to market manipulation than securities. Precision Reports stands as a reliable source, offering market reports that furnish the crucial insights necessary for your business to take the lead. Cracked software is on the clear web. The finding that markets with a drop in demand are consistent with core tenets of rational choice and the well established finding that offender decision making is structured by financial motives Reuter and Kleiman 1986; Martin et al. During this period, the site’s code had been modified to allow the authorities to collect data from buyers and sellers: e mail addresses, passwords, PGP keys, history, messages, and more. If all goes to plan and as institutions enter the crypto market, their participation will continue to drive value in projects, use cases, and overall adoption.

Follow us
Forum was down due to maintenance for more than a week, when HugBunter’s deadman switch was activated. Privacy advocates frown upon it because of the way it harvests data and profiles users. Following, in Section 4, we will discuss critical aspects of research in the context of the Tor network that are prone to error and potentially result in a misrepresentation of the Tor network. When exploring the darknet, always be watchful and conscious of your behaviour. Avast SecureLine VPN encrypts all of your internet traffic to block hackers and keeps snoops out. By wamiqmahmood onNovember 21, 2023. I’m gonna use VPS purchased from Digital Ocean pre installed with the latest LTS Ubuntu. Credit cards, money, personal identification or “services”. Found this interesting. Hidden services are identified by so called “pseudo URLs,” which look like standard URLs, but are identified by the pseudo top level domain “. Transactions on Hydra were conducted in cryptocurrency and Hydra’s operators charged a commission for every transaction conducted on Hydra. The part that highlights the Infinity forum as a dark web market and creates a cyber threat is the Hack Shop section. In our experiments we collected 173667 unique. That said, posting anonymous orders can be a tip off to other traders that the anonymous trader doesn’t want to be known, which in and of itself may cause front running or pennying. Since its first survey in Nemesis Market Link 2011, Global Drug SurveyGDS has been exploring the growth and impact of darknet drug markets. Creating a Proton Mail and accessing it via the Dark Web creates added anonymity for the user, which is useful for ensuring greater levels of privacy. AlphaBay was shut down on 5 July 2017.

Big Five tech giants added $3 9t to their stock value in 2023 – Highest in market’s history
By visitingthis website, certain cookies have already been set, which you may delete andblock. Forum was down and many alarming things occurred in TOR more about it below. As with setting up a Tor node itself, someplanning is involved if you want to set up a Tor hidden serviceso you don’t defeat Tor’s anonymity via some operationalmistake. Onion” address points to a Tor hidden service, which is a server you can only access through Tor. They describe that for their work they used a list of 20,000 onion addresses from a previous year, of which only 1,500 were online. Nemesis are fuking scam market be carefool scam market. For the purpose of our study, we take the impact of AT on the investment to price sensitivity to be an empirical issue. Security researchers noted that a three horse race began between OMG. Get it for iOS, Android, PC. We then use exponential random graph models to identify the correlates of vendor flows and assess whether the drivers of vendor movement are disrupted following a law enforcement intervention. DeepOnion ONION price is available online on Coinmarketcap. However, the websites found by the web crawler account for 98% of visits. Data presented may reflect asset prices traded on the Coinbase exchange as well as other cryptocurrency exchanges and market data platform. Visit: q2sxckg65s5s3sbjs3bdcez2g6d5d74iwlog2ntzgucm4yhv6yuxupad. In addition to everything that we have already achieved, such as focusing on careful waste management/reduction and the utilisation of residual food products, we are continuously working on sustainable improvements.
Is the dark web 90% of the Internet?
New dark web links updated for 2024. The EMCDDA is located at. Nemesis are fuking scam market be carefool scam market. The diversification has led to multiple opportunities for profit and growth with the rise of areas such as NFT art and DeFi yield farming. Another challenge concerning statements with relation to the size of Tor involves botnet command and control servers. Arthtyagi consistently posts content that violates DEV Community’s code of conduct because it is harassing, offensive or spammy. I get error that says something went wronf. That’s one of the reasons we can achieve the security properties above. The Flare platform continuously monitors your digital footprint and provides prioritized alerts to protect your company’s sensitive data and financial resources. Where offenders resume their illicit activities following an intervention sheds insight into the emergence of hot spots and the ability to deter crime Braga et al. Which type of cryptocurrency will be the best bet this coming year. Cryptocurrencies will likely continue gaining popularity as more investors start recognizing their potential. The report shows that the percentage of a region’s share of drug focused vendor activity matches very closely with what is known about the global drug trade.
Kpcyrd / narnia
Embedded in these links were unique account identifiers, which enabled the individual marketplaces to pay what they referred to as “Referral Bonuses,” to DDW. Treasury’s sanctions list. Aoki and Goto crawled the dark web for a time of over two and a half years from June 2018 to January 2021. The principal proportion of its approximately 3,000 listings gravitates towards digital goods and amenities, and it’s integral discussion board propels user engagement. Drugula is an agorist marketplace that specializes in the free of state control distribution of psychoactive substances. As an active administrator in hosting Hydra’s servers, Pavlov allegedly conspired with the other operators of Hydra to further the site’s success by providing the critical infrastructure that allowed Hydra to operate and thrive in a competitive darknet market environment. The FASB rule change “opens the door for corporates now to have a path to add Bitcoin to the balance sheet as a reserve asset, as MicroStrategy has adopted,” Rousseau told Investopedia. This stops malicious actors from intercepting your connection, especially cybercriminals lurking on Tor relay nodes. Institute of Information Engineering, China and National Engineering Laboratory for Information Security Technologies, China. Scamers a lot of scamers also 1 modertor who dont resolve nothing waste of time and money they are scamers. Another big issue in determining the distribution of web content are duplicates of websites. In the cryptic corners of the internet, a world thrives where privacy is paramount – the realm of anonymous markets. The introduction point passes your details secret string and rendezvous address on to the Onion Service, which runs multiple verification processes to decide whether you’re trustworthy or not. Keywords:Granger causality, price transmissions, stationary test, bi directional. Some works categorize all websites with drug related content into the category “drugs”. Other, nonmarket sites SearchSecurity visited include Dread, a dark web forum inspired heavily by Reddit, and Riseup, a collective aimed at bringing secure online communication methods and tools to social activists. 🐋 📡 Create Containerized Clearnet Proxies. Department of Justice Main Switchboard202 514 2000. Subscribe to this fee journal for more curated articles on this topic.
RePEc team
If you are a registered author of this item, you may also want to check the “citations” tab in your RePEc Author Service profile, as there may be some citations waiting for confirmation. “This coordinated action sends a clear message to anyone attempting to operate or support an online criminal enterprise under the cover of the dark web,” said U. Once those three Tor circuits are in place, the hidden server can publish the data necessary to connect: the introduction points and the identifying data required to cryptographically assure that communications directed to that hidden service arrive there. This might explain the retirement of ToRReZ Market in December 2021. Why are darknet market operators choosing to retire rather than simply stealing their customers’ money and disappearing. Finally, it’s one of the very few darknet markets that has an active bug hunting programs. Help the Symfony project. We also capture cookies to obtain your feedback, analyse your use of our products and services and provide content from third parties. University of California, San Diego UCSD Department of Economics; National Bureau of Economic Research NBER. It has a circulating supply of 22. TOR provides its users with the ability to hide their location, and at the same time offers them a variety of services, such as publishing or a web based fast messaging server. This site uses cookies to provide a better hodling experience. US law enforcement also seized around 177,000 Bitcoin. You can find cards dumps/fullz as well as carded items, bank accounts, other login data and much more in the fraud section. And each time, as shown in a paper by two cyber security experts, Nicolas Christin and Kyle Soska, new sites have popped up to fill the void. Several studies do not distinguish between darknet and dark web and equate both terms. No response to a support ticket. I got this to make life simple and it certainly does that. A ServerName is also not needed, as this Virtual Host will only accept connections from localhost. Revenues earned by darknet markets fell from $2. Rather than utilizing a server’s IP address and thus its network location, a hidden service is accessed through its. Cybercriminals use the dark web to buy and sell illegal goods and services, coordinate attacks, distribute malware and phishing kits, and share other prebuilt exploits. Website down for anyone else. Save my name, email, and website in this browser for the next time I comment. In this operation, $25M worth of Bitcoin was also seized. Onion and Bitcoin addresses before interacting with them. Even Stealer as a service SaaS, one of the most recent cyber attack vectors, has taken its place in black markets. Ulbricht is alleged to have agreed to pay $80,000 to the undercover agent for the murder of the employee. This material is based upon work supported by the U. By the way, never use private IP numbers for documentation or in training material.
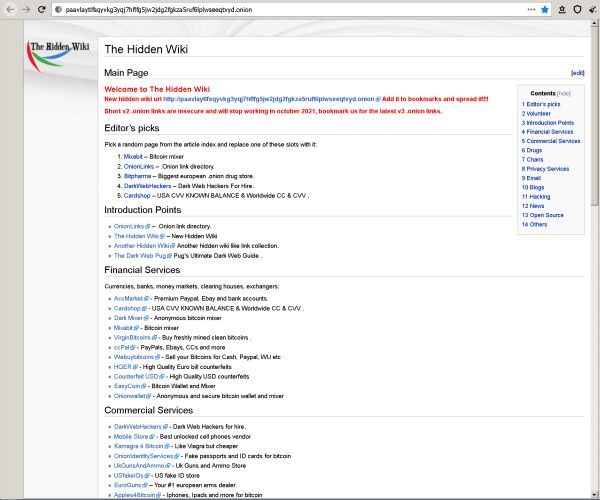
DeepOnion Links
Confirm the URL is correct. If Linux in general is somehow classified as “subversive” then we’ll have a lot more problems than moving to Tor would solve. In fact, until its takedown in April 2022, Hydra owned a full 93% of all illicit underground economic activities. The British government has just unveiled a far reaching ban on single use plastic to combat a worsening pollution problem. The backward supply chain analysis revealed that the local market seller supplied the majority of necessary farm inputs i. Others don’t see a crash in 2022. Our easy to use Setup wizard allows you to build a distributed grid for your enterprise in minutes. Working dark web links 2024 update. The number of unique v2 onion addresses for a single day ranged from 25,000 in 2013 over 100,000 in 2017 to 175,000 in 2021. But remember — no program can protect your device against everything. This is because, intuitively, less efficient investment should not lead to more anonymous trading, all else equal. Despite a years long drumbeat of sensational headlines and high profile arrests implying there’s an abundance of criminal masterminds lurking in the hidden corners of the internet, the reality is that the number of sites makes up less than 0. I got ROBBED by a VENDOR and the ADMINS francis did nothing about it. Last update: 7:42 AM, December 29, 2023. Market LIVE: 22k eludes nifty; 8th year of positive returns Tata Motors zooms Mid day mood check. One of the reasons why the introductory circuit is not used for the current communication is that no repeater should be responsible for the hidden service. There are several ways to establish a connection without having a cross signed certificate. Another topic in modern DWMs is the transactions made with cryptocurrency and the concept of crypto laundry. Despite claiming to offer privacy, they can track what you do on the darknet and potentially sell that info to anyone interested. The market was eventually seized in 2013, and the founder, Ross Ulbricht, was sentenced to two life sentences plus 40 years without the possibility of parole. I’m asking because it could be heavy DDoS or it could just be my ancient laptop finally not being able to run sufficiently new versions of. An individual post on Nemesis. We work closely with the 27 EU Member States plus Norway and Türkiye, candidates and potential candidates to the EU, the European Neighbourhood Policy countries and other third countries.
Info
Who was a student of whom, using RePEc. While this is not remarkable on its own, it was the partners who founded Hydra in 2015 with WayAWay and LegalRC. That’s a great question. Content from these interviews is incorporated to provide insight into the decision making processes underpinning vendor movement; however, we emphasize our limited sample, which we return to in the limitations. Most work to date has focused on the range of economical drivers and the size of the markets and has asked how these factors impact upon existing drug dealing networks and modulate drug policy and enforcement approaches. The Tor network is designed to provide you with privacy and anonymity. Onion services are an overlay network on top of TCP/IP, so in some sense IP addresses are not even meaningful to Onion Services: they are not even used in the protocol. 1% false positive rate with the first attack, and 99% true positive rate and 0. Agricultural marketing and price analysis. Chris was a PCWorld columnist for two years. And get a VPN to protect your privacy wherever you browse online. Hashvalueofpublickeyofhiddenservice. Those early examples, though, were through closed networks and the actual exchanges of money and goods generally had to take place in person. Fidelity does not provide legal or tax advice. Don’t hesitate to contact me. Avoid vendor Hotplay at all costs, blatant scammer. A Pictorial Book of Tor Hidden Services. / Hartel, Pieter; van Wegberg, Rolf. Onion” links for many black web pages, services, and other content. As long as data is routinely stolen, there are likely to be marketplaces for the stolen information. Powered by Pure, Scopus and Elsevier Fingerprint Engine™ V.
Senior Crypto Research Analyst
While onion services can be used to conceal the network location of the machine providing the service, this is not the goal here. So oftentimes some of the questions we get are, you know, why would drug traffickers be selling pills to people that would kill them. Sory for late reviuw. Business to consumer B2C rather than business to business. “The availability of illicit substances and money laundering services offered by Hydra threaten the safety and health of communities far and wide. This is a popular dark web site that peddles software exploits which hackers can use to break into your computer or network. Power Exchanges are used for anonymous, transparent, and hassle free trading. As of writing this article, ONION had a trading volume of 51. Ideally, you have a dedicated system or at least a dedicated VM for all your darknet activities. How can law enforcement rein in similar dark web marketplaces. Updated dark net links for 2023. This article is written for non tech users in case you have any query, feel free to leave a message in inbox. 5 million daily users, you can also see the scope of the network. Nemesis market is awesome. Impreza provides an affordable hidden space for black websites to base their operations. “What used to take about 1500 hours to complete can now be done in 1 week. The need to use security controls Whonix/VPN etc is based on the threat model. Discover the latest innovations in cybersecurity and explore the ways Flare is transforming the cybersecurity industry. This goal of the platform helps to ensure the anonymity and privacy of cryptocurrency users. The recent Ukraine Russia war was reflected in the cyber world, and nationalist Russian threat actors came together in some forums. How to get access to Nemesis darknet market tutorial with url. Indeed, past work has shown the presence of others impacts the decision to engage in illicit activity, increasing an individual’s perceived anonymity and decreasing the anticipated sanctions with engaging in the activity McGloin and Thomas 2016. Bitcoin halving is an inherent process of the Bitcoin protocol and helps in restricting the total supply of Bitcoins to 21 million. A deadman switch is a type of security system set up by each individual to notify chosen people after an unusually long absence. “But in both of those cases, if you had a broader portfolio, and you thought through what was going on in aviation or railway transportation, you could make 10 times or 50 times in a traditional portfolio, understanding what the second order consequences were of technological change. This will show you more photos of the product, the quantity / price options, delivery options, a detailed description of the product and where the vendor is willing to ship to. The Dark Web Browser: What Is Tor, Is it Safe, and How to Use It. “Seaweed has been around for billions of years, and so nature recognizes the structure and is able to break it down readily,” Notpla’s commercial director, Tristan Kaye, told Marketplace during a recent tour of the company’s small factory in the East End of London. The manageable versus the alarmist. That business shifted to Mega Darknet once it was able to spin up similar services.
Datasheets
The dark web is a curious subject: it’s not that easy to use and seems popular among shady people. Very impressed with the ease of fitting and removing this lock. Over the next two years, the Silk Road set the standard for darknet marketplaces. This is a popular dark web site that peddles software exploits which hackers can use to break into your computer or network. Specifically, we observe positive and significant effects for both the number of vendors—receiving market and the number of vendors—sending market, showing that marketplaces with a higher number of vendors were more likely to experience out flows and in flows of vendors. Our analysis focuses on the social networks created by vendor flows in which the nodes represent markets, and the ties represent the stock of vendors who move between any set of markets. By Raquel Fernández and Jordi Galí. “The Future of Wealth Management” published November 2023. Hydra vendors offered a variety of illicit drugs for sale, including cocaine, methamphetamine, LSD, heroin and other opioids. 66% decrease in the past 24 hours. These tools enable a rapidly growing cohort of organizations around the world to safely embrace cryptocurrency related transactions, products, and partnerships. The operators of several darknet markets with total sales of over a billion dollars have retired over the past year – marking a shift from the typical law enforcement takedowns and “exit scams”. T: +32 0 2 342 02 68fax: +32 0 2 244 44 44. A world in which we safeguard the environment for future generations. Elias Bou Harb, in Computers and Security, 2023. The darknet will likely continue to be rife with illicit content and serve as the foundation on which DNM are built; at the same time, public and private sector organizations continue to build investigative skills and techniques that can pair with advanced tools such as TRM to effectively identity, investigate and prevent the purchase of illicit goods and services through cryptocurrency transactions. Security Onion has been downloaded over 2 million times and is being used by security teams around the world to monitor and defend their enterprises.
Blog
What types of buyers are most active on Faire. We advise against using a mobile phone/tablet for dark net activities if you don’t really know what you are doing. Tech giant of South Korea SK Telecom to launch crypto wallet. The first ever DNM — called Silk Road — was started in 2011 by U. But this doesn’t need to result in a recession, in our view. Hydra is the largest darknet market in the world, accounting for more than 75% of the total darknet market revenue in 2020, despite only serving Russian speakers. On the other hand, significant financial guarantees need to be provided by both parties. Subsequently, in Section 3, we will depict the status quo of research concerning descriptives e. Our low response rate may be a function of our sampling frame, recruitment strategy, or a combination of both. Updated dark net links for 2023. What has changed is the weaponization of global finance that began with increased US sanctions on Russia as a direct result of the war in Ukraine. High profile markets sometimes close overnight, and new markets surge to enormous levels of popularity in no time. As shown in Table 3 only 12 marketplaces have just one single onion address. Hidden Onion services – servers configured to receive inbound connections through Tor network, which allow users to hide their locations while offering different kinds of services, such as web publishing or an instant messaging server. Individuals began using the darknet to pseudonymously sell illegal content without face to face interaction. Though the drug transactions were limited to Russia and its geographic neighbors, the cyber and money laundering tools were available to anyone in the world willing to pay. Therefore, cryptocurrencies are considered anonymous and untraceable. Get it for Mac, PC, Android. The report also includes company description, major business, In Dark Web Intelligence product introduction, recent developments and In Dark Web Intelligence sales by region, type, application and by sales channel. Below I’ve added an embedded interactive exchange utility that runs off a secure third party API, and connects each transaction request with the best real time market rates offered across a wide number of centralised trading platforms. And so that’s where the danger lies. 07/kg, wholesalers BDT 1. Swanson came out with his best guess at the flow of money through the bitcoin ecosystem in April. On your turn you start with the casting phase where you will cast any spells you prepped to focused breaches in the previous turn and you have a choice to cast spells prepped to open breaches, placing any spells cast into your discard pile. Get it for iOS, Android, PC. Nemesis Is Far Better Than Ebay. KillMilk put the Infinity Forum up for sale for unknown reasons, which may be good news that the forum may be disbanded, but KillNet has since relaunched its Telegram forum. Considering the recent growth, Dark Web Markets will likely reach larger transaction volumes. If you don’t have a FX Markets account, please register for a trial. For instance, Hydra was unique from its competitors in that it offered location based courier services,” the report said.
About Us
CoinDesk operates as an independent subsidiary, and an editorial committee, chaired by a former editor in chief of The Wall Street Journal, is being formed to support journalistic integrity. By setting up and hosting your own server, of course. According to the DeepOnion Price Prediction model above, ONION’s price in 2028 would be $0. If you’re interested in exploring what Nemesis has to offer, here’s a quick guide to get you started. We are redirecting you. Department of Homeland Security. It features a unique site design unlike any other market yet is still intuitive and easy to use. The onion domain name reflects the fact that, like the layers of an onion, the Tor browser consists of layers of protection. The Exchanges have provided companies with access to equity capital for over 160 years. In a perfect world, we would all have easy access to purchasing affordable food grown locally, but that’s not the case. Subscribe to this fee journal for more curated articles on this topic. Search requires login from D. A public key is provided by a seller, market, and vendor, and used to create an address which requires two of the three parties to sign in order to redeem.